Search Results
Showing results 1 to 5 of 5

Public Key Encryption: Kid Krypto
Source Institutions
In this activity, learners conduct a simulation exercise related to public key encryption and try to intercept a message sent between two learners.

Fingerprint Identification
Source Institutions
In this activity (on page 2) about fingerprint analysis, learners use graphite from a pencil and scotch tape to capture their fingerprints.
Cryptographic Protocols: The Peruvian Coin Flip
Source Institutions
This activity about cryptographic techniques illustrates how to accomplish a simple, but nevertheless seemingly impossible task—making a fair, random choice by flipping a coin between two people who d

Information Hiding: Sharing Secrets
Source Institutions
This activity about cryptographic techniques illustrates a situation where information is shared, and yet none of it is revealed.
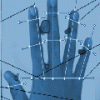
Hand Biometrics Technology
Source Institutions
In this activity, learners explore how engineers incorporate biometric technologies into products as well as the challenges of engineers who must weigh privacy, security and other issues when designin
