Search Results
Showing results 1 to 6 of 6

Public Key Encryption: Kid Krypto
Source Institutions
In this activity, learners conduct a simulation exercise related to public key encryption and try to intercept a message sent between two learners.

The Muddy City: Minimal Spanning Trees
Source Institutions
In this puzzle, learners investigate the decisions involved in linking a network between houses in a muddy city.
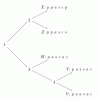
Phylogenetics
Source Institutions
This activity lets learners participate in the process of reconstructing a phylogenetic tree and introduces them to several core bioinformatics concepts, particularly in relation to evolution.

Divide and Conquer: Santa's Dirty Socks
Source Institutions
This activity introduces the idea of "divide and conquer" using a fictitious but serious problem--a pair of dirty socks has accidentally been wrapped in one of the presents that Santa is about to deli

Unlocking the Secret in Product Codes
Source Institutions
In this activity, learners will explore how product barcodes are scanned accurately and be able to "guess" the last number in a 13 digit barcode correctly every time.
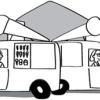
Tourist Town: Dominating Sets
Source Institutions
In this activity, learners use a fictitious map of "Tourist Town" and counters to problem solve how to place ice-cream vans on street intersections so that every other intersection is connected to one
