Search Results
Showing results 1 to 12 of 12

From the Internet to Outer Space
Source Institutions
In this activity, learners will use Google Sky to observe features of the night sky and share their observations.

Public Key Encryption: Kid Krypto
Source Institutions
In this activity, learners conduct a simulation exercise related to public key encryption and try to intercept a message sent between two learners.

Artificial Intelligence: The Intelligent Piece of Paper
Source Institutions
This activity explores what it means for a computer to be intelligent and introduces the topic of what a computer program is and how everything computers do simply involves following instructions writ
Cryptographic Protocols: The Peruvian Coin Flip
Source Institutions
This activity about cryptographic techniques illustrates how to accomplish a simple, but nevertheless seemingly impossible task—making a fair, random choice by flipping a coin between two people who d

The Turing Test: Conversations with Computers
Source Institutions
This activity aims to stimulate discussion on the question of whether computers can exhibit “intelligence,” or are ever likely to do so in the future.

Information Hiding: Sharing Secrets
Source Institutions
This activity about cryptographic techniques illustrates a situation where information is shared, and yet none of it is revealed.
Passion for Pixels
Source Institutions
In this technology activity, learners explore digital imaging and pixels. Learners "transmit" an image to a partner by creating an image on grid paper.

EEEEK--A Mouse!
Source Institutions
In this activity, learners explore the concept of how engineering solved the problem of human/computer interface.
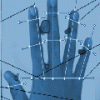
Hand Biometrics Technology
Source Institutions
In this activity, learners explore how engineers incorporate biometric technologies into products as well as the challenges of engineers who must weigh privacy, security and other issues when designin

Space Weather Action Center
Source Institutions
In this interdisciplinary activity, learners create a Space Weather Action Center (SWAC) to monitor solar storms and develop real SWAC news reports.
Forward Thinking
Source Institutions
In this activity, learners create their own weather forecast map.

String Thing
Source Institutions
String Thing is an interactive online game in which learners change a virtual string's tension, length, and gauge to create different musical pitches.
