Search Results
Showing results 1 to 11 of 11

Public Key Encryption: Kid Krypto
Source Institutions
In this activity, learners conduct a simulation exercise related to public key encryption and try to intercept a message sent between two learners.

Battleships: Searching Algorithms
Source Institutions
This activity explores the main algorithms that are used as the basis for searching on computers, using different variations on the game of battleships.
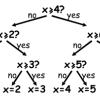
Twenty Guesses: Information Theory
Source Institutions
This activity introduces the idea that computer scientists measure information by how "surprising" a message is.

The Muddy City: Minimal Spanning Trees
Source Institutions
In this puzzle, learners investigate the decisions involved in linking a network between houses in a muddy city.
Phylogenetics
Source Institutions
This activity lets learners participate in the process of reconstructing a phylogenetic tree and introduces them to several core bioinformatics concepts, particularly in relation to evolution.

Divide and Conquer: Santa's Dirty Socks
Source Institutions
This activity introduces the idea of "divide and conquer" using a fictitious but serious problem--a pair of dirty socks has accidentally been wrapped in one of the presents that Santa is about to deli
Cryptographic Protocols: The Peruvian Coin Flip
Source Institutions
This activity about cryptographic techniques illustrates how to accomplish a simple, but nevertheless seemingly impossible task—making a fair, random choice by flipping a coin between two people who d

Unlocking the Secret in Product Codes
Source Institutions
In this activity, learners will explore how product barcodes are scanned accurately and be able to "guess" the last number in a 13 digit barcode correctly every time.

Information Hiding: Sharing Secrets
Source Institutions
This activity about cryptographic techniques illustrates a situation where information is shared, and yet none of it is revealed.
Tourist Town: Dominating Sets
Source Institutions
In this activity, learners use a fictitious map of "Tourist Town" and counters to problem solve how to place ice-cream vans on street intersections so that every other intersection is connected to one

Sound Representation: Modems Unplugged
Source Institutions
In this activity, learners listen to songs and decode hidden messages based on the same principle as a modem. As a final challenge, learners decode the binary messages in a music video.
