Search Results
Showing results 1 to 20 of 48

Public Key Encryption: Kid Krypto
Source Institutions
In this activity, learners conduct a simulation exercise related to public key encryption and try to intercept a message sent between two learners.

Battleships: Searching Algorithms
Source Institutions
This activity explores the main algorithms that are used as the basis for searching on computers, using different variations on the game of battleships.

Guess My Number
Source Institutions
In this game, learners experience how computers divide a big problem into many smaller ones and how they use binary "yes"/"no" questions.
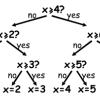
Twenty Guesses: Information Theory
Source Institutions
This activity introduces the idea that computer scientists measure information by how "surprising" a message is.

The Muddy City: Minimal Spanning Trees
Source Institutions
In this puzzle, learners investigate the decisions involved in linking a network between houses in a muddy city.

Programming Languages: Harold the Robot
Source Institutions
In this activity related to computer programming, learners give directions to a "robot" (either an adult or another learner) and find out which instructions the robot is able to follow, and how their

Wash This Way
Source Institutions
In this activity on page 4 of the PDF, learners investigate the importance of washing their hands.

Decode the Barcode
Source Institutions
In this online activity, learners crack the special code imprinted on envelopes to help the U.S. Postal Service deliver the mail.
Phylogenetics
Source Institutions
This activity lets learners participate in the process of reconstructing a phylogenetic tree and introduces them to several core bioinformatics concepts, particularly in relation to evolution.

Binary Challenge
Source Institutions
In this activity, learners cut out 5 paper cards and label them with 1, 2, 4, 8, or 16 dot(s) to explore binary digits.

Divide and Conquer: Santa's Dirty Socks
Source Institutions
This activity introduces the idea of "divide and conquer" using a fictitious but serious problem--a pair of dirty socks has accidentally been wrapped in one of the presents that Santa is about to deli

Artificial Intelligence: The Intelligent Piece of Paper
Source Institutions
This activity explores what it means for a computer to be intelligent and introduces the topic of what a computer program is and how everything computers do simply involves following instructions writ
Ice Roads: Steiner Trees
Source Institutions
In this outdoor activity, learners use pegs (like tent pegs) and string or elastic to simulate drill sites and roads in Northern Canada.

What am I?
Source Institutions
In this activity, learners examine nanoscale structures of common things.

Coding Algorithms
Source Institutions
In this activity, learners will code an algorithm to make it through a maze.

Metal Heads
Source Institutions
Pairs of learners play the roles of programmer and robot. The programmer gives specific directions to the robot to accomplish a simple task (e.g. walk across the room and pick up a pencil).

Squeezing Pictures Into Codes
Source Institutions
In this activity, learners will explore how computers represent pictures using pixels.

Code Cracker
Source Institutions
Whether it's the genetic code, an ancient language, or patterns of light in a distant galaxy, scientists often have to play the role of decoder.
Cryptographic Protocols: The Peruvian Coin Flip
Source Institutions
This activity about cryptographic techniques illustrates how to accomplish a simple, but nevertheless seemingly impossible task—making a fair, random choice by flipping a coin between two people who d

Unlocking the Secret in Product Codes
Source Institutions
In this activity, learners will explore how product barcodes are scanned accurately and be able to "guess" the last number in a 13 digit barcode correctly every time.
