Search Results
Showing results 1 to 16 of 16

Battleships: Searching Algorithms
Source Institutions
This activity explores the main algorithms that are used as the basis for searching on computers, using different variations on the game of battleships.

The Muddy City: Minimal Spanning Trees
Source Institutions
In this puzzle, learners investigate the decisions involved in linking a network between houses in a muddy city.

The Poor Cartographer: Graph Coloring
Source Institutions
In this activity, learners help a poor cartographer color in the countries on a map, making sure each country is colored a different color than any of its neighbors.

Information Hiding: Sharing Secrets
Source Institutions
This activity about cryptographic techniques illustrates a situation where information is shared, and yet none of it is revealed.
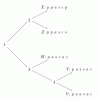
Phylogenetics
Source Institutions
This activity lets learners participate in the process of reconstructing a phylogenetic tree and introduces them to several core bioinformatics concepts, particularly in relation to evolution.

How Much is a Name Worth?
Source Institutions
In this math lesson, learners use simple addition facts to compute values (in dollars and cents) for their names.

Program a Friend
Source Institutions
In this activity (on page 2), one person "programs" the other like a robot to move through a space, trying to get them to avoid obstacles and reach a goal.

Get In The Game
Source Institutions
In this design challenge, learners will use computational thinking to design their own board game.
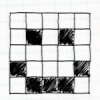
Passion for Pixels
Source Institutions
In this technology activity, learners explore digital imaging and pixels. Learners "transmit" an image to a partner by creating an image on grid paper.
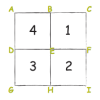
Solving Playground Network Problems
Source Institutions
In this activity, learners use cooperation and logical thinking to find solutions to network problems on the playground.

The Orange Game: Routing and Deadlock in Networks
Source Institutions
When a lot of people share one network (such as cars using roads, or messages getting through the Internet), there is the possibility that competing processes will create a “deadlock," or an interrupt
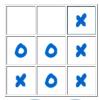
Tic-Tac-Toe
Source Institutions
In this online version of the classic paper and pencil game, learners practice looking ahead to anticipate an opponent's move.
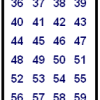
Guesswork
Source Institutions
In this number puzzle/trick, learner #1 thinks of a number between 1 and 63. Learner #2 shows learner #1 six cards and asks them whether the cards contain their number.

Geometry and Spatial Relations: Mirror, Mirror
Source Institutions
In this math lesson, learners use hinged mirrors to discover that regular polygons are composed of triangles tessellating around a center point.

A-Mazing Robot
Source Institutions
This activity lets you program your 'robot' (a willing friend) to pick up and dispose of some 'toxic waste' using as few commands as possible.

Secret Writing Devices
Source Institutions
In this activity about encryption, learners cut out a secret decoder badge from a handout and use it to encode messages to each other.
