Search Results
Showing results 1 to 18 of 18

Public Key Encryption: Kid Krypto
Source Institutions
In this activity, learners conduct a simulation exercise related to public key encryption and try to intercept a message sent between two learners.

Battleships: Searching Algorithms
Source Institutions
This activity explores the main algorithms that are used as the basis for searching on computers, using different variations on the game of battleships.
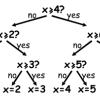
Twenty Guesses: Information Theory
Source Institutions
This activity introduces the idea that computer scientists measure information by how "surprising" a message is.

The Poor Cartographer: Graph Coloring
Source Institutions
In this activity, learners help a poor cartographer color in the countries on a map, making sure each country is colored a different color than any of its neighbors.

The Muddy City: Minimal Spanning Trees
Source Institutions
In this puzzle, learners investigate the decisions involved in linking a network between houses in a muddy city.
Phylogenetics
Source Institutions
This activity lets learners participate in the process of reconstructing a phylogenetic tree and introduces them to several core bioinformatics concepts, particularly in relation to evolution.

Divide and Conquer: Santa's Dirty Socks
Source Institutions
This activity introduces the idea of "divide and conquer" using a fictitious but serious problem--a pair of dirty socks has accidentally been wrapped in one of the presents that Santa is about to deli
Ice Roads: Steiner Trees
Source Institutions
In this outdoor activity, learners use pegs (like tent pegs) and string or elastic to simulate drill sites and roads in Northern Canada.
Cryptographic Protocols: The Peruvian Coin Flip
Source Institutions
This activity about cryptographic techniques illustrates how to accomplish a simple, but nevertheless seemingly impossible task—making a fair, random choice by flipping a coin between two people who d

Sound Representation: Modems Unplugged
Source Institutions
In this activity, learners listen to songs and decode hidden messages based on the same principle as a modem. As a final challenge, learners decode the binary messages in a music video.

How to Train Your Robot
Source Institutions
In this activity, learners discover that training a robot can be hard work! Learners investigate how robots complete a task by following a list of sequential instructions.

Card Flip Magic: Error Detection & Correction
Source Institutions
This magic trick is based on how computers detect and correct data errors.
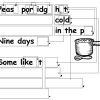
You Can Say That Again!: Text Compression
Source Institutions
This activity helps students learn how computers "compress" text by identifying repeating patterns of letters, words, and phrases.
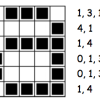
Colour by Numbers: Image Representation
Source Institutions
This activity shows learners how computers use numbers to represent pictures. A grid is used to represent the pixels (short for picture elements) of a computer screen.

Secret Writing Devices
Source Institutions
In this activity about encryption, learners cut out a secret decoder badge from a handout and use it to encode messages to each other.

Paint by the Numbers
Source Institutions
In this pencil and paper activity, learners work in pairs and simulate how astronomical spacecraft and computers create images of objects in space.
Forward Thinking
Source Institutions
In this activity, learners create their own weather forecast map.

Cipher Wheel
Source Institutions
In this activity, learners make their own encrypted code to pass along secret messages using a printable cipher wheel.
