Search Results
Showing results 1 to 20 of 42

From the Internet to Outer Space
Source Institutions
In this activity, learners will use Google Sky to observe features of the night sky and share their observations.

Public Key Encryption: Kid Krypto
Source Institutions
In this activity, learners conduct a simulation exercise related to public key encryption and try to intercept a message sent between two learners.

Battleships: Searching Algorithms
Source Institutions
This activity explores the main algorithms that are used as the basis for searching on computers, using different variations on the game of battleships.
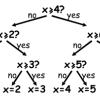
Twenty Guesses: Information Theory
Source Institutions
This activity introduces the idea that computer scientists measure information by how "surprising" a message is.

The Poor Cartographer: Graph Coloring
Source Institutions
In this activity, learners help a poor cartographer color in the countries on a map, making sure each country is colored a different color than any of its neighbors.

Pico Cricket Compass
Source Institutions
Learners can program a compass to draw a circle by itself using a Pico Cricket, some Legos, and lots of tape! Pico Cricket is required.
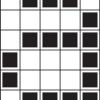
Color by Numbers: Image Representation
Source Institutions
Computers store drawings, photographs, and other pictures using only numbers. Through this activity, learners decode numbers to create pictures using the same process that computers use.

LEGO Robots
Source Institutions
This activity (on page 2 of the PDF under GEMS Activity) is a full inquiry investigation into technology design and testing.

The Muddy City: Minimal Spanning Trees
Source Institutions
In this puzzle, learners investigate the decisions involved in linking a network between houses in a muddy city.

Count the Dots: Binary Numbers
Source Institutions
Data in computers is stored and transmitted as a series of zeros and ones. Learners explore how to represent numbers using just these two symbols, through a binary system of cards.
Human Interface Design: The Chocolate Factory
Source Institutions
In this activity about human interface design issues, learners help the Oompa-Loompas of a great chocolate factory solve different problems.
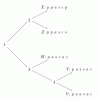
Phylogenetics
Source Institutions
This activity lets learners participate in the process of reconstructing a phylogenetic tree and introduces them to several core bioinformatics concepts, particularly in relation to evolution.

Programming Languages: Marching Orders
Source Institutions
In this activity about computer programming, learners follow instructions in a variety of ways in order to successfully draw figures.

Divide and Conquer: Santa's Dirty Socks
Source Institutions
This activity introduces the idea of "divide and conquer" using a fictitious but serious problem--a pair of dirty socks has accidentally been wrapped in one of the presents that Santa is about to deli

Artificial Intelligence: The Intelligent Piece of Paper
Source Institutions
This activity explores what it means for a computer to be intelligent and introduces the topic of what a computer program is and how everything computers do simply involves following instructions writ
Ice Roads: Steiner Trees
Source Institutions
In this outdoor activity, learners use pegs (like tent pegs) and string or elastic to simulate drill sites and roads in Northern Canada.

What am I?
Source Institutions
In this activity, learners examine nanoscale structures of common things.
Cryptographic Protocols: The Peruvian Coin Flip
Source Institutions
This activity about cryptographic techniques illustrates how to accomplish a simple, but nevertheless seemingly impossible task—making a fair, random choice by flipping a coin between two people who d

Unlocking the Secret in Product Codes
Source Institutions
In this activity, learners will explore how product barcodes are scanned accurately and be able to "guess" the last number in a 13 digit barcode correctly every time.

The Orange Game: Routing and Deadlock in Networks
Source Institutions
When a lot of people share one network (such as cars using roads, or messages getting through the Internet), there is the possibility that competing processes will create a “deadlock," or an interrupt
