Search Results
Showing results 1 to 20 of 21

Artificial Intelligence: The Intelligent Piece of Paper
Source Institutions
This activity explores what it means for a computer to be intelligent and introduces the topic of what a computer program is and how everything computers do simply involves following instructions writ

Battleships: Searching Algorithms
Source Institutions
This activity explores the main algorithms that are used as the basis for searching on computers, using different variations on the game of battleships.

Divide and Conquer: Santa's Dirty Socks
Source Institutions
This activity introduces the idea of "divide and conquer" using a fictitious but serious problem--a pair of dirty socks has accidentally been wrapped in one of the presents that Santa is about to deli

The Muddy City: Minimal Spanning Trees
Source Institutions
In this puzzle, learners investigate the decisions involved in linking a network between houses in a muddy city.

Sound Representation: Modems Unplugged
Source Institutions
In this activity, learners listen to songs and decode hidden messages based on the same principle as a modem. As a final challenge, learners decode the binary messages in a music video.
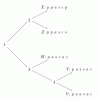
Phylogenetics
Source Institutions
This activity lets learners participate in the process of reconstructing a phylogenetic tree and introduces them to several core bioinformatics concepts, particularly in relation to evolution.
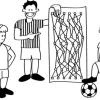
Cryptographic Protocols: The Peruvian Coin Flip
Source Institutions
This activity about cryptographic techniques illustrates how to accomplish a simple, but nevertheless seemingly impossible task—making a fair, random choice by flipping a coin between two people who d

EEEEK--A Mouse!
Source Institutions
In this activity, learners explore the concept of how engineering solved the problem of human/computer interface.

Program a Friend
Source Institutions
In this activity (on page 2), one person "programs" the other like a robot to move through a space, trying to get them to avoid obstacles and reach a goal.

How to Train Your Robot
Source Institutions
In this activity, learners discover that training a robot can be hard work! Learners investigate how robots complete a task by following a list of sequential instructions.

Cipher Wheel
Source Institutions
In this activity, learners make their own encrypted code to pass along secret messages using a printable cipher wheel.

Get In The Game
Source Institutions
In this design challenge, learners will use computational thinking to design their own board game.
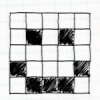
Passion for Pixels
Source Institutions
In this technology activity, learners explore digital imaging and pixels. Learners "transmit" an image to a partner by creating an image on grid paper.
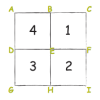
Solving Playground Network Problems
Source Institutions
In this activity, learners use cooperation and logical thinking to find solutions to network problems on the playground.

Tiny Particles, Big Trouble!
Source Institutions
In this activity, learners discover why some nanoscale science and technology is done in the controlled environment of a clean room, what clean rooms are like, and how scientists help keep the clean r
Team Up: Fun With Division
Source Institutions
In this activity, learners will divide into teams or groups of equal size. “How many teams of three can we make?” “We need an equal number of children at each of the four computers.
Tic-Tac-Toe
Source Institutions
In this online version of the classic paper and pencil game, learners practice looking ahead to anticipate an opponent's move.
Art Cars
Source Institutions
In this activity, learners design miniature cars. Learners can create a telephone car, soccer car, merry-go-round car, or any other theme car they can imagine.

Metal Heads
Source Institutions
Pairs of learners play the roles of programmer and robot. The programmer gives specific directions to the robot to accomplish a simple task (e.g. walk across the room and pick up a pencil).
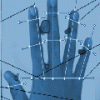
Hand Biometrics Technology
Source Institutions
In this activity, learners explore how engineers incorporate biometric technologies into products as well as the challenges of engineers who must weigh privacy, security and other issues when designin
